![Net Core JWT Authentication [Step By Step Tutorial] - .Net Core JWT Token - ASP.Net Core 5 JWT - YouTube Net Core JWT Authentication [Step By Step Tutorial] - .Net Core JWT Token - ASP.Net Core 5 JWT - YouTube](https://i.ytimg.com/vi/3Q_aNm6gJiM/maxresdefault.jpg)
Net Core JWT Authentication [Step By Step Tutorial] - .Net Core JWT Token - ASP.Net Core 5 JWT - YouTube
GitHub - maltesander/rest-jersey2-json-jwt-authentication: This example project shows how to work with jersey2, jwt token authentication and role annotations
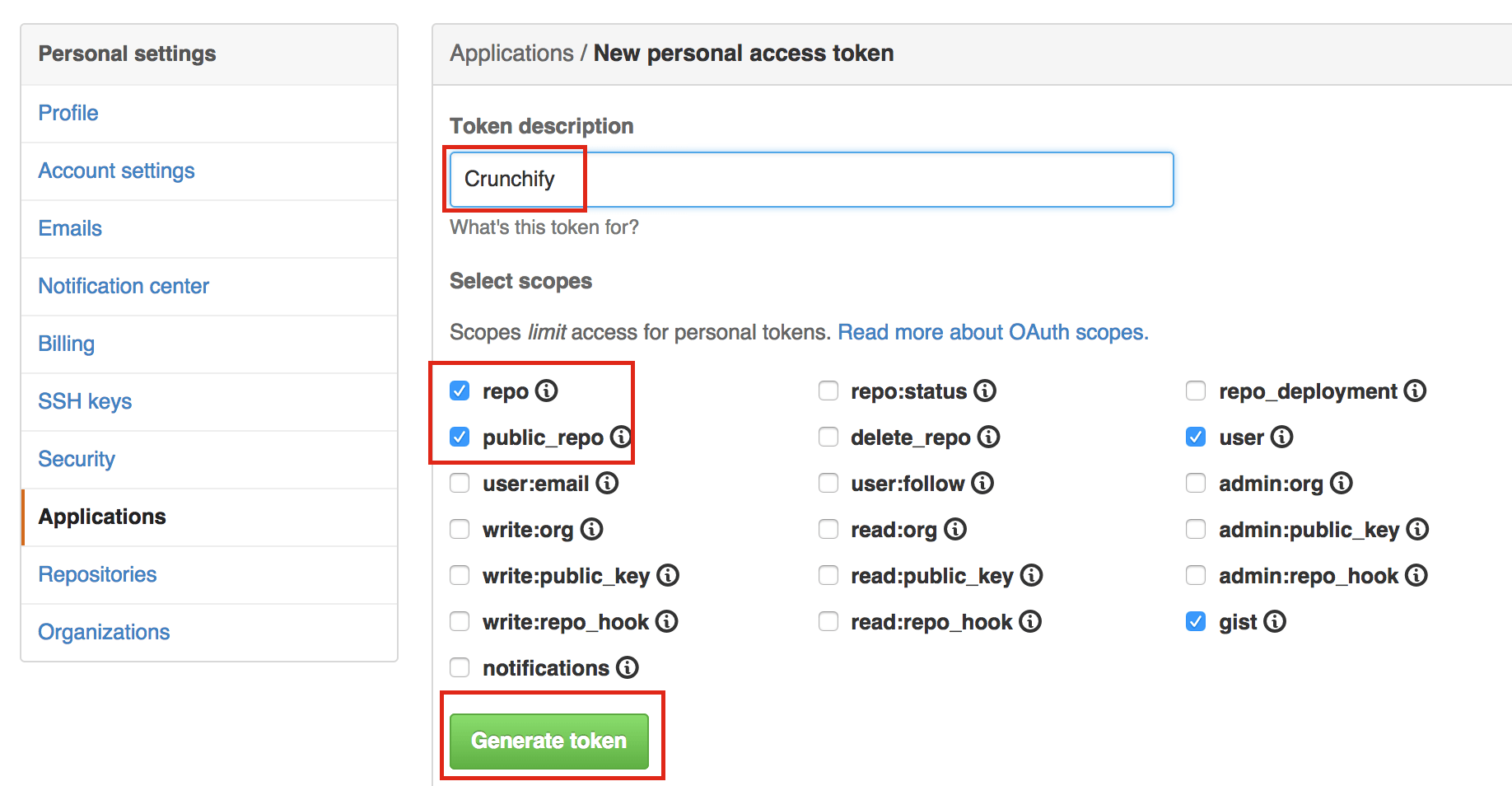
How to Access Github Content with Basic OAuth Authentication in Java? HTTPClient Or URLConnection Method • Crunchify

JAX-RS Security using JSON Web Tokens (JWT) for Authentication and Authorization – Developers Corner – Java Web Development Tutorials